
Hacking Car Cameras Through The Cloud
Intro As the entire world races torwards connectivity, time-to-market is often prioritized over security. In today’s episode - finding vulnerabilities in smart car appliences! If you recognize one...

Intro As the entire world races torwards connectivity, time-to-market is often prioritized over security. In today’s episode - finding vulnerabilities in smart car appliences! If you recognize one...
Prologue It all started when I got fed up with the typical Linux process injection PoCs that relied on either ptrace() or LD_PRELOAD. I wanted something different, something a bit more intriguing—a...

As security researchers, we are often required to think creatively in order to think of edge cases and find vulnerabilities. Creativity is commonly referred to as the attribute of ‘non-systematical...

Imagine you have received a WhatsApp message with a link to ln.instagram.com. Where do you think the link leads? Instagram? Think again. I have found a phishing vulnerability in WhatsApp that enab...
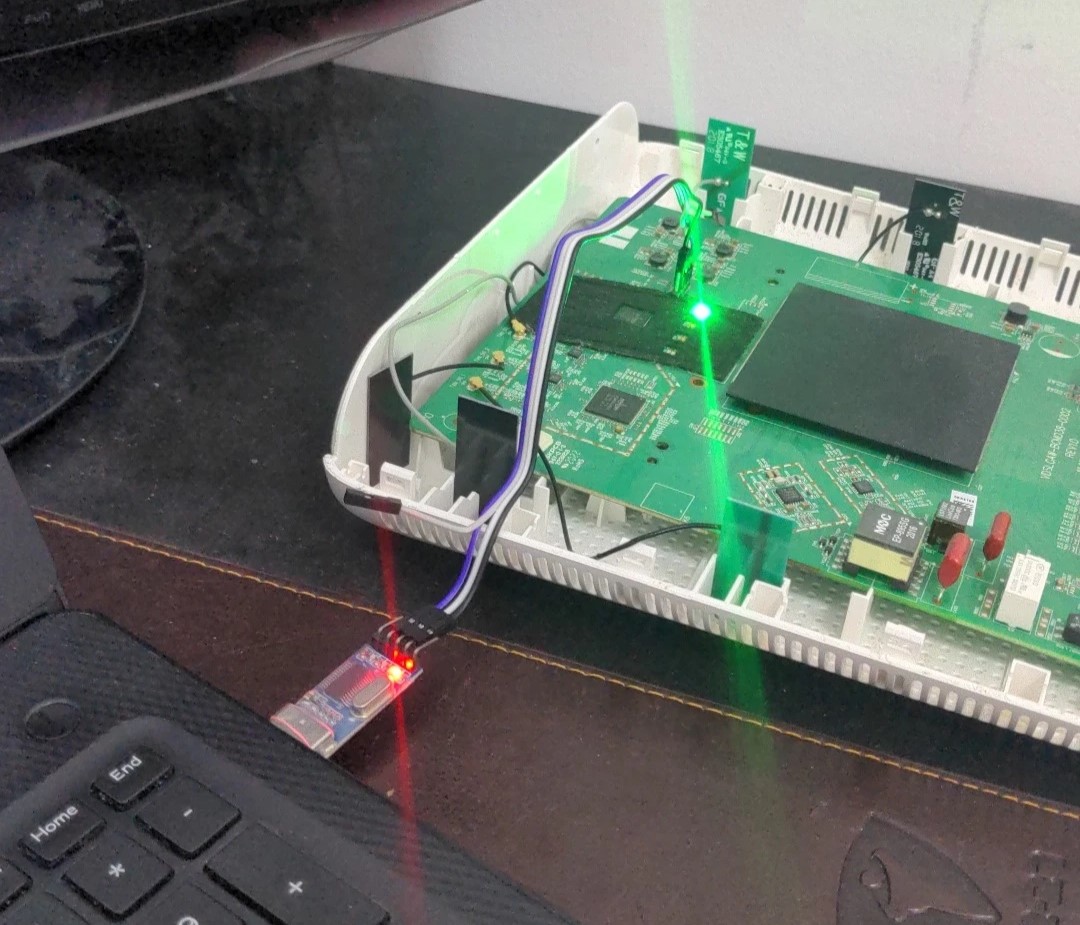
There is a saying that you don’t truly own a router until you flash your own firmware on it. The only problem was that the bootloader of my router was password protected. So I accepted the challeng...
Intro There is a saying that you don’t truly own a router until you root it. So i accepted the challenge with my ISP’s router. This is the same router from my previous posts a customized Broadcom B...
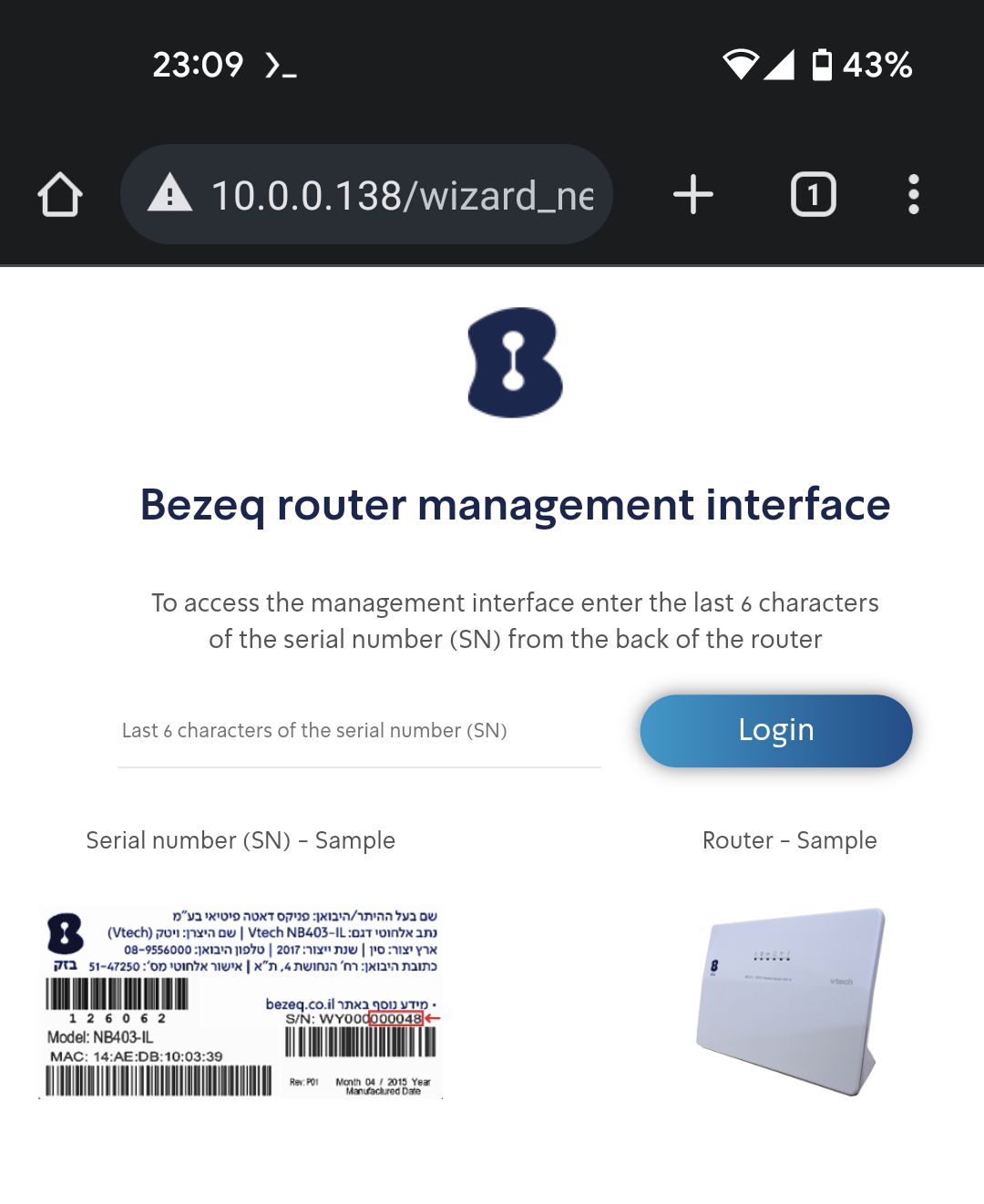
Intro I want to share with you a cute little vulnerability I found (CVE-2022-47848). Two models of Bezeq’s routers, Vtech NB603-IL and Vtech IAD604-IL are vulnerable to authentication bypass. The v...
We are now living in an era where publicly available models of AI are capable of finding vulnerabilities in code and exploiting them for free! As you may have heard, OpenAI has recently released a...

Intro Today I want to talk with you about physical security and showcase some examples of security flaws. Although many times it does not feel like it, we still live in a physical world where damag...
One of the reasons I love being a security researcher is that the foolish and curious child in me never dies. I frequently ask myself what would happen if I did this and that. The other day I ente...